Wednesday, 20 April 2016
How safe is airline passenger data? Not secure at all.
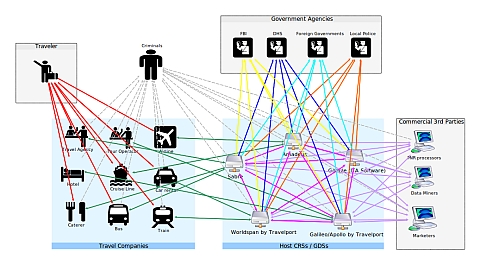
[PNR data flows. Each node in the network is a point of vulnerability. Click image for larger version.]
This week in the German IT news portal Golem and the German weekly news magazine Die Zeit, Hauke Gierow has a deep dive, based in substantial part on a long interview with me, into the security vulnerabilities that affect passenger name record data:
- Wer wo welche Daten über Passagiere sammelt und wie
- Wo also liegen die Informationen zu meinem Flug?
- Kein Rechtsschutz für EU-Bürger
- Video interview with German voiceover translation: Wie sicher sind Fluggastdaten
- Longer raw video of interview in English: How secure are airline passenger data?
- Alternate version in Zeit Online: “Rein in die Blackbox” (PDF)
Only a few of the many vulnerabilities and methods of attack I know about are discussed in the articles and interview. It would be moderately hard for an attacker to obtain PNR data in bulk, but easy to obtain PNR data about an individual targeted victim or small group of victims.
The published articles and video on Golem.de and Zeit.de are, of course, in German, but Golem has kindly made available a ten-minute excerpt from the original raw video of the interview with me in English that provides a good introduction to the issue.
I’ve been talking and writing about these vulnerabilities for at least 15 years. But few other journalists have reported on the (in)security of the commercial computerized reservation systems (CRSs) that host PNR data, even when I’ve highlighted it in interviews and articles. Although most of the CRSs are based in the USA, the best (although less detailed or technical) previous report on this issue in English was in the Brussels-based New Europe newsmagazine.
Most of the publicity and public debate about PNR data, including the debate and vote last week in the European Parliament has concerned the mirror copies of PNR data held by governments. Those government mirror copies are vulnerable to different types of abuse. But ironically, government mirror copies of PNRs are typically more securely held, and less widely distributed or easily accessible, than the original master copies of PNRs stored and retained — even after copies are sent to governments — in the commercial global cloud of CRSs.
The threats I’m most concerned about come from stalkers and perpetrators of domestic violence, although there are also threats of identity theft, industrial espionage, etc.
Any attempt to regulate or protect government copies of PNR data is built on a foundation of sand, and doomed to be ineffective, as long as the CRSs that store the master commercial copies of PNRs are fundamentally insecure, and as long as privacy and data protection authorities (in countries that have them, unlike the US) fail to sanction CRSs and the airlines, travel agencies, tour operators, and other travel companies that use them for their flagrant, systematic violations of privacy and security norms and laws.
Link | Posted by Edward on Wednesday, 20 April 2016, 12:03 (12:03 PM)