Tuesday, 27 December 2016
"Travel data: fraud with booking codes is too easy"
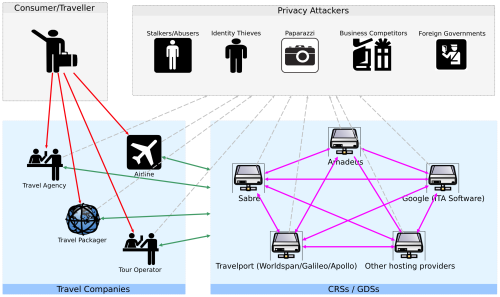
[Some of the privacy and security threats to PNR data and the CRS network, from my testimony in 2013 as an invited expert witness before the Advisory Committee on Aviation Consumer Protection of the U.S. Department of Transportation. Click image for larger version.]
Video, slides, and blog post of presentation by SRLabs at 33C3
(27 December 2016, Hamburg, Germany)
Who’s watching you while you travel?
(details of this vulnerability published on my Web site, 18 April 2002)
Flight booking systems lack basic privacy safeguards, researchers say
(by Eric Auchard, Reuters, 27 December 2016)
Reisedaten: Betrug mit Buchungscodes ist zu einfach
(by Patrick Beuth, Zeit, 26 December 2016)
Unsicherheit bei Flugbuchungen: “Greift mehr Legacy-Systeme an”
(by Hauke Gierow, Golem.de, 28 December 2016)
Une étude alerte sur les failles des réservations de vol
(by Alexis Orsini, Numerama.com, 28 December 2016)
33C3: Gravierende Sicherheitslücken bei Reisebuchungssystemen
(by Stefan Krempl, Heise Online, 28 December 2016)
Amadeus-Sicherheitsproblem: Einladung für Cyber-Vandalen
(by Frank Patalong, Der Spiegel, 27 December 2016)
Today at the 33rd Chaos Communication Congress (33C3) in Hamburg, Germany, white-hat hackers from Security Research Labs inspired by news reports in Germany about my work will publicly demonstrate their ability to access and alter other people’s airline reservations (PNRs) by exploiting vulnerabilities including ones that I wrote about and called to the attention of all of the four major Computerized Reservation Systems in 2002, but that the CRSs have made a deliberate choice not to close because (a) government authorities have not enforced existing data protection laws (in other countries than the USA, which has no such laws) against CRSs, airlines, or travel agencies, and (b) these travel companies put their profits ahead of passengers’ privacy and security.
There’s been some advance coverage in German print (mentioning my work) and television news media. (Zeit, Handelsblatt, Der Spiegel.) But the CRS exploits discussed in these news stories are not the most serious of those that I expect the folks from SRLabs (well-known for their previous public exploits) to demonstrate at 33C3. Watch the livestream here at 21:45 CET in Hamburg, 12:45 p.m. PST in San Francisco. Recorded video will be posted later, but I don’t know how soon. I’ll add a link once it is available.
As I wrote in my book, The Practical Nomad Guide to the Online Travel Marketplace, which was published in early 2001 before 9/11, “Privacy is the Achilles heel of Internet travel planning.” In that book (page 121), I also wrote about the vulnerability of the public Web gateways operated by CRS companies — the vulnerability exploited in today’s demonstration at 33C3, of which the first was Sabre’s VirtuallyThere.com:
If you make reservations through Travelocity.com or any other Sabre travel agency, you can view your itinerary at Sabre’s “Virtually There” Web site (www.virtuallythere.com) by entering your last name and the six-character “record locator”” for your reservations. This is good if you’ve misplaced your printed itinerary, but at present is dangerously insecure. Anyone who sees your name and record locator on an itinerary (through a window envelope, for example, or over your shoulder in an airport check-in line) can find out your home address, the exact dates you”ll be away, where you are staying, etc. Properly secured, it could be a great feature, and hopefully Travelocity.com will have secured it before you read this. If they haven’t, don”t make any reservations in Sabre until they do, unless you want every detail of your trip to be public.
At the time that this was written and this book went to press in 2000, I was already in active discussions with Sabre about this issue. Eventually Sabre made some partial improvements, which I reported on in 2002, but they were insufficient and in any event proved to be temporary.
After each of the other CRS companies launched sites imitating VirtuallyThere.com, and with the same vulnerabilities, and none of them responded to my repeated requests for comment about those vulnerabilities, I went into more detail in an online supplement to the book in 2002:
What else has changed in 2001-2002, since “The Practical Nomad Guide to the Online Travel Marketplace”… went to press? Here are a few of the trends, changes, and news items I think are most significant for consumers and travellers:…
The security and privacy vulnerabilities of the three main Internet itinerary viewing services, VirtuallyThere.com (Sabre), ViewTrip.com (Galileo/Apollo), and CheckMyTrip.com (Amadeus) have not been corrected as of March 2002. I mentioned these in “The Practical Nomad Guide to the Online Travel Marketplace”, but I didn’t highlight them in the book because I assumed that they would soon be fixed. More than a year later, that hasn’t happened.
These services currently do not use secure or secret passwords, and pose an extreme risk of severe privacy invasion. Even if you don’t use these services yourself, they make complete details of your itinerary available to anyone who knows your last name and reservation number (“record locator”). Reservation numbers are printed conspicuously on itineraries, and are often visible through window envelopes, or to “shoulder surfers” in check-in lines or any other public place where you might have your itinerary in view. It’s fairly obvious that no one who designed these services gave any real thought to their privacy implications (which is typical of Internet services).
Most online and offline travel agencies use either Sabre, Galileo/Apollo, or Amadeus, so you may not be able to avoid having your itinerary revealed in this way….
I urge consumers to complain to Sabre, Galileo, and Amadeus. Demand that they change their security procedures before a stalker, abuser, or kidnapper takes advantage of one of these services.
In comments submitted to a privacy roundtable convened by the U.S. Federal Trade Commission in 2009 and co-signed by organizations including the Consumer Travel Alliance (Travelers United) and the Consumer Federation of America, I wrote:
Travel records are highly vulnerable to unauthorized access….Because no logs are normally kept of access to PNRs or customer profiles stored in a CRS/GDS,… unauthorized access… could go undetected indefinitely.
CRS’s/GDS’s have deployed insecure public Web gateways that allow anyone who knows your name and “record locator” to view the complete itinerary from your PNR. But a “record locator” is not a password and does not provide adequate access control: record locators are printed and displayed everywhere from itineraries and tickets to boarding pass stubs (frequently discarded after a flight) and the tags on checked luggage, which are exposed to public scrutiny, unattended, while on the carousel at the destination waiting to be claimed….
The absence of access logs in the major CRS’s/GDS’s makes it impossible for travel companies that use these systems to comply with the fundamental principles of fair information practices — or even, in many cases, their own claimed privacy policies. Since no access logs are kept or included in PNRs, travel companies themselves don’t know who has accessed data they entered. As they have admitted in response to some of our requests, they don’t know and thus can’t tell consumers who has accessed data about them, which data, or from where in the world.
I’m available today from San Francisco for interviews by e-mail, phone, or video Skype before or after the 33C3 session. I’ll also be in Europe for two weeks in late January and early February, possibly with some time in Germany. I’d be happy to participate in public discussions of this issue, or to meet privately with anyone from a CRS or data protection authority who wants to talk about what can and should be done. If you are interested, please get in touch.
In the meantime, here are answers to some of the most frequently-asked questions I’ve been getting in the last few days:
Is the biggest threat to the privacy and security of Passenger Name Record (PNR) data governmental, commercial, or criminal? All of the above.
When I first got interested in the privacy of travel data in the late 1990s, while I was working with CRSs and PNR data in the airline reservation industry, I already knew that CRSs were vulnerable to hacking. But my initial privacy concern was primarily with criminal stalking and with data mining and exploitation of personal travel information for marketing and commercial purposes. Metadata about the movement of your physical body is just as sensitive as telecom metadata about the movement of your messages, or more so. Commercial and criminal exploitation of PNR data is at least as serious a threat as government access to, or use of, this data.
But since 9/11, the focus of public, political, and media attention has been on government access to and use of PNR data. Little attention has been paid to the commercial abuse of travel data, and the vulnerability of PNR data stored by CRSs to intrusion and illicit exploitation, that predated 9/11 and has continued unabated.
Government surveillance and control of travel remains as much of a threat as ever, of course. But I will be very pleased if, as a result of the public demonstration of CRS vulnerabilities by SRLabs, these longstanding commercial and criminal vulnerabilities and threats begin to get some of the attention they have long warranted.
Have you written or spoken publicly about the vulnerabilities demonstrated today by SRLabs, and/or others? Yes. For example (in addition to the discussion quoted above form my 2001 book and 2002 online update):
- Who’s watching you while you travel? (18 April 2002; this article goes into detail about a specific vulnerability demonstrated today by SRLabs)
- Total Travel Information Awareness: Travel Data and Privacy (an earlier version of this article won a Lowell Thomas Travel Journalism Award Award for investigative reporting from the Society of American Travel Writers Foundation in 2003, which I mention not so much to boast about the award but as an indication that this article wasn’t obscure or unnoticed at the time it was published)
- What’s in a Passenger Name Record (PNR)? (“CRSs can be, and have been, hacked. It’s actually quite easy to hack a CRS and obtain PNR data without being detected. I’d be happy to discuss some of the vulnerabilities I know about with any CRS operator, airline, legislator, or data protection official who is willing to listen.”)
- Identity theft from a discarded boarding pass (3 May 2006; linking to this article in the Guardian)
- Fasten your seatbelts: Information security and the travel industry (Interview with InfoSecurity magaizine, 2009. “In general, you don’t need much information in order to access a particular passenger’s airline booking - on Travelport’s ViewTrip site, for example, just the record locator and last name will unlock the full itinerary details…. Hasbrouck believes that… ‘If it were more widely recognised, I think the industry would be more freaked out about the potential liability. I hope it doesn’t take a widely publicised fiasco.’”)
- The privacy problems of travel data (My 2009 submission to the U.S. Federal Trade Commission discussing CRS and PNR security and privacy defects including Web gateways “secured” only by insecure record locators, lack of access logs, and insufficiently granular access controls)
- Talk at Re:Publica, Berlin, 16 April 2010 (See slides re: “Unexplored hacking possibilities”)
- Talk at the c-base hackerspace, Berlin, 20 October 2011 (slides; “PNR data in the CRS ‘cloud’: Cloud storage = risk of ‘leakage’ of data, violation of privacy.”)
- Consumer privacy and air travel (My 2013 testimony as an invited expert witness before the Advisory Committee on Aviation Consumer Protection of the U.S. Department of Transportation, including a summary of vulnerabilities and needed technical and policy fixes)
Has your analysis of PNR and CRS vulnerabilities been reported in major news media? Yes. For example:
- Covering the Traveler’s Electronic Trail: Practical Nomad author Edward Hasbrouck lays out the case that these enormously intimate records are too important not to protect (Bloomberg/Business Week, 2003; “We’re in more danger from identity theft and stalking than from airline terrorism…. You also need to regulate the use of [travel] data … by private companies — especially the [information in] computerized reservation systems, which are central to the problem. They play the same role as central data repositories of credit bureaus do for financial data. But they have been largely invisible.”)
- Air-travel data puts Europeans at risk of identity theft: Is system open to spooks and crooks? (by Andy Carling, New Europe, 2011)
- Wie sicher sind Fluggastdaten? (by Hauke Gerow, Golem.de, 2016)
How long have CRSs been aware of these vulnerabilities? When I wrote this article in 2002 I contacted each of the four major CRSs for comment. Each of them, starting with Sabre’s VirtuallyThere.com, had recently launched a similar Web gateway to their PNR database that used a widely-disseminated non-changeable six-character “record locator” in place of a password. Of the big four CRS companies, only Sabre was willing to talk to me. Sabre made minor temporary changes to their Web gateway, but it has repeatedly reverted to its previous insecure mode of operation. The other CRSs ignored my vulnerability report and published discussion of it.
Has anyone from a travel company or government data protection authority ever approached you about your reports of CRS vulnerabilities? No.
How often have these vulnerabilities been exploited? We don’t know, and we can’t know, because CRSs don’t keep access logs. In my experience, the most common real-world threats to travellers are stalking, harassment, and domestic violence. Those attackers who are detected are usually trying to get access to PNR data through pretexting. (I used to train travel agents to be alert to the possibility of this sort of pretexting.) There could be many other motives for a targeted attempt to get access to info about the travel of a specific person.
Other attack methods, such as those demonstrated by SRLabs at CCC, are less likely to be detected. We would be unlikely to know about attacks using these methods unless an attacker (a) was caught by other means, and (b) confessed to their mode of attack.
Are these vulnerabilities inherent in “legacy” CRS architecture? No. Sabre has demonstrated that a user-selected access password can be stored within the data structure of an existing “legacy” CRS. All major CRSs create and maintain an immutable permanent change log (“history”) within each PNR, and there is an obvious pathway to expansion of the same functionality and data structure to log accesses as well as changes.
Why haven’t CRSs fixed these vulnerabilities? CRSs don’t see any profit in reducing risks to passengers’ privacy and security. Their customers (airlines and travel agencies, not travellers) haven’t demanded or offered to pay for it. And governments haven’t forced them to do it.
Travel companies care about threats to their money, not threats to individual travellers’ privacy or security. They will deny this, but their decades of failure to address these well-known and well-publicized vulnerabilities prove that this is true.
CRSs don’t deal directly with travellers, so it should be no surprise that CRSs are completely clueless when it comes to modeling threats to travellers’ privacy and security — not that they are usually trying to do so.
What about airlines and travel agencies? Airlines and travel agencies outsource the hosting of their customer data to the CRSs, using the CRS as an outsourced cloud software-as-a-service transaction data and CRM system (developed and in use decades before any of this terminology). Airlines and travel agencies can deploy their own or third-party systems to interact with PNRs stored in the CRSs. But airlines and travel agents depend on the CRSs for basic database security. If the CRSs allow access to PNRs without a password and without logging that access, airlines and travel agencies can’t do anything about that vulnerability. An airline or travel agency could threaten to switch to another CRS, but that would do no good if none of the major CRSs offer passwords, access logs, or other security features.
Airlines also have a financial stake in systems that sacrifice passengers’ privacy and security to cut airline costs. Airlines have been able to lay off tens of thousands of employees by getting passengers to check in online and print their own boarding passes, instead of having that done by airline check-in staff. If having to remember and enter a password that isn’t printed on their itinerary like the current record locator discourages passengers from checking themselves in online, it will cost airlines money. And if there’s a choice between simple, insecure procedures that maximize the percentage of self check-in, and more secure procedures that result in a slightly higher percentage of passengers checking in with airline staff, airlines will choose more automation over more passenger privacy, every time.
For decades, “security” for airlines and travel agencies was about physical security of printed, individually numbered and accountable blank ticket stock, and airline validation plates used for imprinting tickets, which were required to be kept under lock and key or in safes meeting specified standards for theft resistance. The closed private CRS network was similarly protected through the physical security of the leased-line communication channels and the locks and keys on the doors of airline and travel agency offices with CRS terminals. Like the replacement of paper tickets with e-tickets, outsourcing all this infrastructure to commodity PCs connected to CRS hosts over the public Internet saved CRSs too much money to be held back by the need for a reassessment of the security model required by the new architecture.
The existing cloud of CRS hosts was opened up to access over the public Internet with no thought to the security implications of that change.
Is this legal? In the USA, yes, since the USA has no data protection or privacy law applicable to airlines (or most other commercial data). In some other countries, no. There are data protection rules, including a requirement for adequate technical measures and security policies, in the European Union’s Code of Conduct for CRSs. The European Commission has the authority to investigate and enforce these rules, and fine CRSs up to 10% of their gross annual revenues for violations. Laws in Canada, the European Union, and some other countries require CRSs, airlines, and travel agencies, like other businesses, to provide individuals with a list of the third parties to whom their data has been transferred. Without logs of who has retrieved PNRs from the CRSs, it’s impossible for any travel company to provide such an accounting of disclosures. If asked, they just make something up about who they think was supposed to have accessed your PNR data, since they don’t really know.
Have you complained to data protection authorities? Yes. I have made complaints against Air Canada, Air France, KLM, and Lufthansa, after taking flights on each of these airlines, to the data protection authorities in their home countries.
Have these authorities taken any action as a result of your complaints? No. My complaints have all been dismissed.
What do you think should have been done? Back in the 1990s, when data protection laws and regulations requiring an accounting of disclosures were adopted in Canada and the European Union, airlines and travel agencies that operate in Canada and/or the EU should have realized that compliance with these new laws would require new CRS functionality, including access logging. They should have insisted that any CRS that wanted to continue to serve airline offices or travel agencies in those countries implement the capabilities needed to comply with the law. If they didn’t, CRSs and the travel companies that use them should have been among the first targets for enforcement of these data protection laws. But since there was no effort to enforce these laws, travel companies had no financial incentive to spend money on compliance, and made no changes.
Why haven’t government authorities taken any action against travel companies that don’t protect passenger data? This is the most difficult of these questions for me to answer. I have to speculate, but I suspect that the largest factors are (a) lack of technical expertise about CRSs and airline reservations by the data protection authorities, so that they don’t feel confident in challenging or rejecting airline lies that would not be credible to technical experts, and (b) reluctance (especially in case of technical doubt) to order actions that would be costly to economically and symbolically significant national airlines.
What can we do about this? The initial heavy lifting has to be done by the CRSs, to implement basic PNR security features such as user-selected passwords and immutable access logging. Since CRSs are B2B companies, consumers have little direct influence on their actions. In theory, travellers could try to pressure airlines and travel agencies to demand action by the CRSs, but I don’t think that has much chance of success.
In the USA, as I’ve been saying for many years, we need a Federal privacy law applicable to airline reservations and other commercial travel data. We’ll get a law like that restricting the ability of travel companies to monetize the information about us that they think of as “their” data, not ours, only if we organize to demand it from Congress. But realistically, that’s not going to happen soon, with the former owner of a failed airline who has appointed the former owner of another failed airline to oversee the further deregulation of businesses like theirs, about to take office as President of the USA.
The most likely path to reform leads from public pressure and complaints to action by the data protection authority in some country that has a privacy law that requires adequate data access controls and accounting for disclosures of data (which is only possible if PNR access is logged).
Every major airline has appointed agents who subscribe to each of the big four CRSs. So if any one airline is forced by national authorities to upgrade its data security, it will have to get all four major CRSs to make the necessary changes, or lose the business of all of that airlines’ agents to competing CRSs. And once system functionality is upgraded for one airline and/or for CRS users in one country, there’s no reason for the CRS not to offer it to all airlines, CRS offices, and CRS subscribers worldwide.
Airlines and CRSs will act only when either (a) some government orders them to do so, and enforces those orders by jailing executives who don’t comply or collecting fines large enough to affect executives’ bonuses and investors’ confidence in the stock, or (b) public pressure forces them to do so following a scandal when some murderous stalker confesses that they tracked down their former domestic partner and killed them and/or their children by obtaining illicit access to PNR data.
I hope that (a) comes before (b).
Link | Posted by Edward on Tuesday, 27 December 2016, 02:54 ( 2:54 AM)"Flight booking systems lack basic privacy safeguards, researchers say" (by Eric Auchard, Reuters, 27 December 2016):
http://uk.reuters.com/article/us-cyber-travel-idUKKBN14G1I6
"Amadeus is assessing the findings of SR Labs on travel industry security," a company spokeswoman told Reuters.
"We will take these findings into account and work together with our partners in the industry to address the issues that have been exposed here and seek solutions to potential problems," she said, referring to airlines and other travel industry partners.
"As a matter of course Amadeus does protect its systems, including Check My Trip, from the type of automated robotic attacks outlined in this report."
Sabre told Reuters: "We have numerous layers of security in place. Discussing how we maintain security and the privacy of travelers undermines those safeguards and the security of our systems."
Travelport [which operates both Worldspan and Galileo/Apollo] did not respond to a request for comment....
LONG-KNOWN VULNERABILITIES
Nohl said the vulnerabilities he found with travel databases are not new. They have been described, conceptually, by San Francisco-based travel privacy campaigner Edward Hasbrouck, who has waged a sometimes lonely campaign to expose them for years.
Hasbrouck, author of the 2001 traveler's rights book "The Practical Nomad Guide to the Online Travel Marketplace", said that since the 9/11 airline attacks on U.S. cities, industry and public attention has focused on government access to travel data to insure flight safety instead of such data’s commercial abuse.
Fifteen years ago, he warned: "Privacy is the Achilles' heel of Internet travel planning".
Hasbrouck said the SRL research vindicates his arguments.
"If the data protection laws that have been in effect since the early 1990s in the EU and Canada had been enforced, (travel systems) would have been required to make changes that would have significantly reduced some of the vulnerabilities... that SRLabs has now demonstrated can be exploited", he said.
Posted by: Edward Hasbrouck, 27 December 2016, 10:41 (10:41 AM)Archived HD video (stream or download):
https://media.ccc.de/v/33c3-7964-where_in_the_world_is_carmen_sandiego
Also in streaming format on Youtube:
https://www.youtube.com/watch?v=m6IgrMCMW8k
Follow-up, 30 December 2016:
CRS/GDS companies and travellers' privacy
https://hasbrouck.org/blog/archives/002280.html
I went through some of your talks, and now I'm not sure: what parts are new in Nohl & Nikodijevic talk at 33C3 compared to your findings?
@axl - Good question.
These vulnerabilities are well known. But I think 3 things are new in the presentation at 33C3:
(1) I explained that this was possible. They actually did it, on stage, in real time.
(2) I discussed how easy it is to find out the record locator for a PNR. They showed how to find a record locator by brute force (trial and error).
(3) They showed how to obtain a record locator from a bar code on a boarding pass or baggage tag. This was discussed in the "Krebs On Security" blog in 2015:
https://krebsonsecurity.com/2015/10/whats-in-a-boarding-pass-barcode-a-lot/
Posted by: Edward Hasbrouck, 3 January 2017, 13:00 ( 1:00 PM)"Travel Booking Systems Expose User Data: Researchers" (by Eduard Kovacs, SecurityWeek, 2 January 2017):
http://www.securityweek.com/travel-booking-systems-expose-user-data-researchers
...SecurityWeek has reached out to Amadeus, Sabre and Travelport for comment. Travelport believes the research is flawed and misleading.
"Cyber security and the privacy of customer data are critical priorities for Travelport and an area in which we invest extensively in and lead in," Travelport said in an emailed statement. "As such, we make ongoing investments in our own systems, and also engage with the various industry bodies we participate in, to implement any changes recommended in support of the general digital travel booking ecosystem. In recognition of our focus in this area, earlier this year, we were the first GDS to be certified for ISO 27001 compliance, an industry standard acknowledging our commitment to responsibly manage both our data and that of our customers worldwide."
Sabre says it has numerous layers of security in place, but the company believes that discussing how it maintains the security and privacy of travelers undermines those safeguards and the security of its systems.
"Amadeus has upgraded security to its own properties, and will continue to defend against 'brute force attacks'," an Amadeus spokesperson told SecurityWeek. "We are also assessing broader industry issues and will work with our partners to address these and seek solutions to potential problems.”="
Travel expert Edward Hasbrouck has been trying to raise awareness of these weaknesses since 2002, but he says service providers have only taken limited steps to address the issues.
Posted by: Edward Hasbrouck, 4 January 2017, 07:27 ( 7:27 AM)thx for your reply!
Posted by: axl, 9 January 2017, 03:26 ( 3:26 AM)Follow-up, 12 January 2016:
"What can I do to protect my PNR data?":
https://hasbrouck.org/blog/archives/002281.html
Posted by: Edward Hasbrouck, 12 January 2017, 19:42 ( 7:42 PM)Follow-up, 18 January 2017:
"Unresponsive 'comments' from Amadeus":
https://hasbrouck.org/blog/archives/002283.html
International Travel & Health Insurance Journal (17 January 2017):
https://www.itij.com/story/13014
"Researchers, including Edward Hasbrouck -- who has been campaigning on the issue for several years -- have called for airlines to adopt modern safeguards, such as limiting the number of PNR requests per internet address and offering passengers a changeable password, to try to protect travellers from these threats."
Posted by: Edward Hasbrouck, 19 January 2017, 21:10 ( 9:10 PM)https://www.justice.gov/usao-ndga/pr/west-african-computer-hacker-sentenced-federal-prison
"West African computer hacker sentenced to Federal Prison" (press release frrm the U.S. Attorney's Office, Northern District of Georgia, 5 June 2017):
"Eric Simeu was responsible for a series of 'phishing campaigns' which targeted customers of Global Distribution System ('GDS') companies from approximately July 2011 to September 2014. The GDS companies impacted by Simeu’s criminal conduct included Travelport... and Sabre....
"Simeu's phishing campaigns targeted customers of Travelport and Sabre, causing phishing emails to be delivered to their customers for the purpose of obtaining and stealing their unique log-in credentials. Simeu and others used the stolen log-in credentials to access the servers of Travelport and Sabre and cause the issuance of fraudulent airline tickets...."
Posted by: Edward Hasbrouck, 8 October 2018, 09:36 ( 9:36 AM)https://link.springer.com/article/10.1007%2Fs10611-018-9777-8
https://doi.org/10.1007/s10611-018-9777-8
"Leaving on a jet plane: the trade in fraudulently obtained airline tickets", by Alice Hutchings (Department of Computer Science & Technology, University of Cambridge, Cambridge, UK), published in "Crime, Law and Social Change", 8 May 2018
Posted by: Edward Hasbrouck, 8 October 2018, 10:01 (10:01 AM)